Understanding SSH - A Deep Dive into Secure Shell
Introduction
Secure Shell (SSH) is one of the most widely used protocols for securely accessing networked computers. Originally developed as a replacement for less secure remote login methods like Telnet, SSH has become the de facto standard for encrypted connections over insecure networks. This deep dive explores how SSH works under the hood, from key exchange to encrypted communication, and explains the different layers and mechanisms that ensure secure data transmission.
What is SSH?
SSH, or Secure Shell, is a cryptographic network protocol that enables secure communication between two networked devices. It provides confidentiality, integrity, and authentication for data exchanged between a client and a server. SSH is primarily used for remote login and command execution, tunneling, and file transfers. Unlike traditional protocols, SSH uses encryption and digital keys to establish a secure communication channel, ensuring that data cannot be intercepted or modified.
SSH Protocol Layers
The SSH protocol is built in layers, with each layer providing specific functionality to ensure a secure communication channel. The three main layers are:
- Transport Layer: The transport layer provides server authentication, confidentiality, and integrity. It sets up encryption through the use of symmetric and asymmetric key exchange and ensures that data integrity is maintained using Message Authentication Codes (MACs).
- Authentication Layer: The authentication layer verifies the identity of the user trying to access the server. This is typically done through password-based or public key-based authentication. Public key authentication is more secure and involves the use of asymmetric key pairs.
- Connection Layer: The connection layer is responsible for managing multiple logical channels over a single SSH connection. Each channel may serve a different purpose, such as remote command execution, tunneling, or file transfer via SCP/SFTP.
SSH Key Exchange
The SSH key exchange process is the foundation of secure communication. During key exchange, both client and server agree on a shared secret that will be used to encrypt communication. SSH typically uses the Diffie-Hellman key exchange algorithm to achieve this. The steps involved are:
- Step 1: The client and server each generate public and private key pairs.
- Step 2: The client sends its public key to the server, and the server responds with its public key.
- Step 3: Both parties use the received public keys and their own private keys to compute a shared secret, which is used for symmetric encryption of subsequent communication.
Encryption and Authentication
SSH uses both symmetric and asymmetric encryption to secure data. Symmetric encryption (e.g., AES) is used to encrypt the data itself, while asymmetric encryption (e.g., RSA) is used during the key exchange and authentication processes. Once the shared secret is established, symmetric encryption ensures that all data exchanged between client and server is confidential.
Authentication in SSH can be achieved through passwords or public key authentication. Public key authentication is preferred as it is less susceptible to brute force attacks. In public key authentication, the server verifies the identity of the client by checking the client’s private key against its authorized keys list.
Data Integrity and MAC
Ensuring data integrity is crucial in preventing data tampering during transit. SSH uses Message Authentication Codes (MAC) to achieve this. After data is encrypted, a MAC is generated for each data packet using a secret key known only to the client and server. This MAC is sent along with the encrypted packet, allowing the receiving end to verify its authenticity.
SSH Connection Protocol
The SSH connection protocol operates on top of the transport and authentication layers, enabling the creation of multiple logical channels over a single connection. Each channel serves a different purpose, such as executing commands, transferring files, or forwarding ports. These channels are managed efficiently, allowing users to establish multiple secure communication streams over the same SSH connection.
SSH Port Forwarding
SSH port forwarding allows secure tunneling of network connections over an encrypted SSH channel. This is useful for securely accessing services or systems that are behind a firewall or otherwise unreachable from the client. SSH supports three types of port forwarding: local, remote, and dynamic. Each of these options provides flexibility in forwarding traffic securely.
SCP and SFTP with SSH
SSH also provides secure file transfer capabilities through SCP (Secure Copy Protocol) and SFTP (Secure File Transfer Protocol). SCP allows for copying files between a local and a remote host using SSH, while SFTP provides a more interactive file transfer session, similar to FTP, but over an encrypted SSH channel. Both SCP and SFTP use SSH to ensure data confidentiality and integrity during transfers.
Visual Representation of SSH
Below is an image that visually explains the SSH key exchange process and how encryption works during an SSH session.
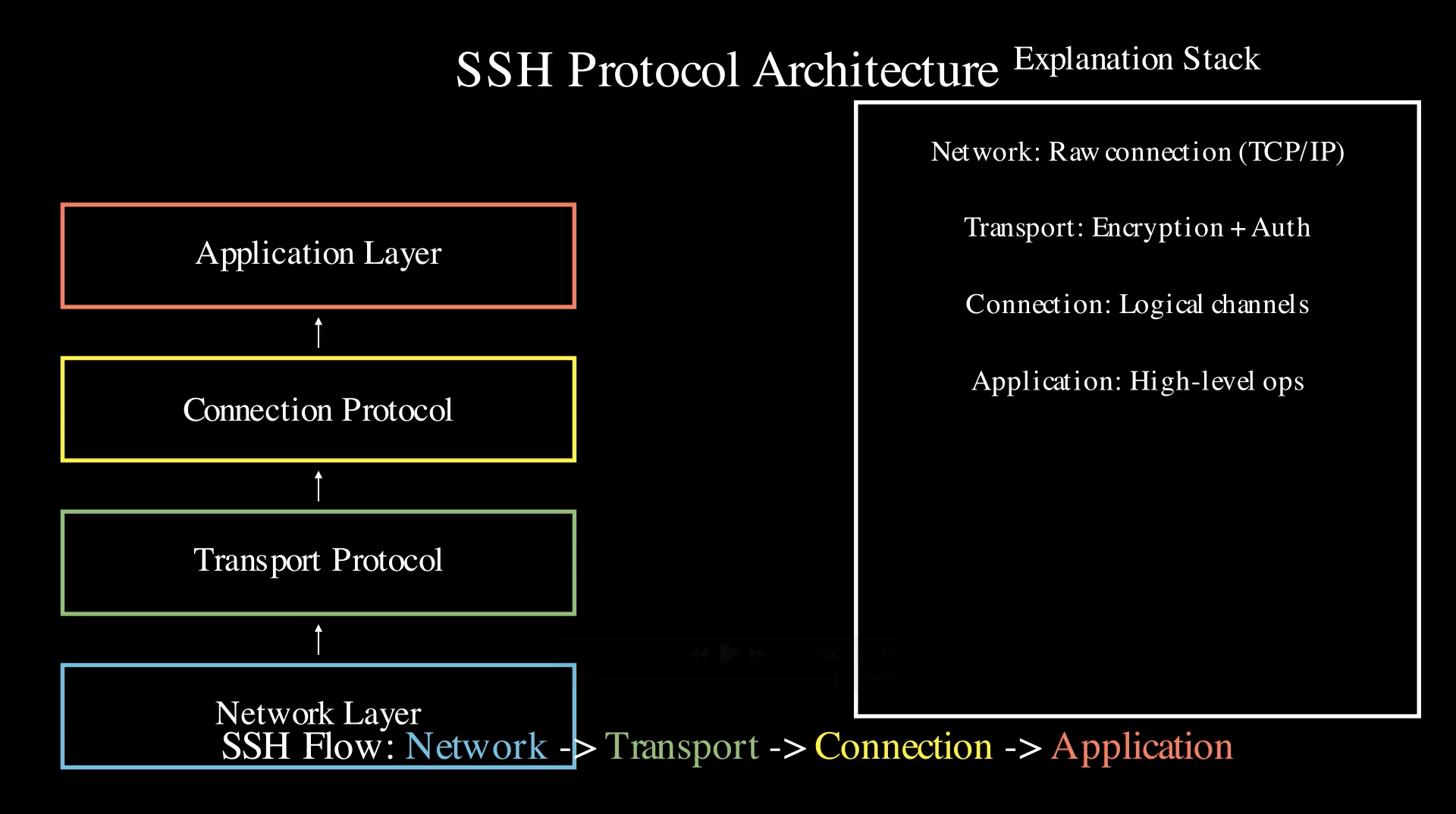
Figure 1: An illustrative diagram of the SSH key exchange process, showing the interaction between client and server to establish a secure connection.
Conclusion
SSH provides a robust and secure means of accessing remote systems, with encryption, authentication, and data integrity all built-in. Understanding how SSH works under the hood—especially the key exchange, encryption, and channel management mechanisms—helps in appreciating the protocol's security benefits and recognizing why it is widely used for secure remote communication.
Whether you are managing servers, tunneling traffic, or transferring files, SSH is a versatile tool that ensures your data remains secure and your identity is protected. The various layers of the SSH protocol work in concert to provide confidentiality, integrity, and authenticity, making SSH a cornerstone of secure system administration.